Empower Your Service WITh Reliable IT Support Providers and Cyber Safety Solutions
In today's quickly advancing digital landscape, the foundation of an effective company hinges on the smooth integration of dependable IT support services and durable cybersecurity options. With the exponential growth of online hazards and the increasing intricacy of technological systems, services encounter a pressing need to strengthen their facilities versus possible susceptabilities. By entrusting your IT requires to qualified specialists and applying positive cybersecurity actions, you can protect your operations, secure sensitive data, and maintain an one-upmanship in the marketplace. The secret to opening the full possibility of your organization exists in the tactical alignment of innovation with your organizational objectives, ensuring a resistant and protected structure for sustained development.
Significance of Reliable IT Support
In today's digitally-driven business landscape, the value of trusted IT support can not be overstated. Businesses depend heavily on innovation to operate successfully and effectively. From maintaining networks to fixing technical issues, having dependable IT support makes certain that procedures run smoothly without considerable interruptions.
Among the primary reasons that reputable IT support is important is its role in decreasing downtime. Any kind of technical problem or system failing can stop business procedures, causing shed productivity and earnings. With prompt and efficient IT support, these issues can be dealt with swiftly, reducing downtime and its linked expenses.
Moreover, reputable IT support plays a vital function in improving cybersecurity. In an age where cyber hazards are rampant, having a group of IT professionals makes certain that systems are sufficiently protected from potential breaches. These specialists implement durable safety steps, display systems for any questionable activities, and supply prompt updates to protect versus developing cyber risks.

Advantages of Cybersecurity Solutions
Offered the vital function of trusted IT support in reducing downtime and improving cybersecurity, it is necessary to highlight the substantial advantages that cybersecurity solutions bring to services in today's digital landscape. Cybersecurity services play an essential duty in securing delicate data and shielding organizations from cyber risks.
Cybersecurity options enable services to discover and respond to cyber events immediately, lessening the impact of prospective safety and security breaches. Inevitably, investing in cybersecurity services not just safeguards businesses from cyber hazards however also contributes to their lasting sustainability and growth in a significantly digital globe.
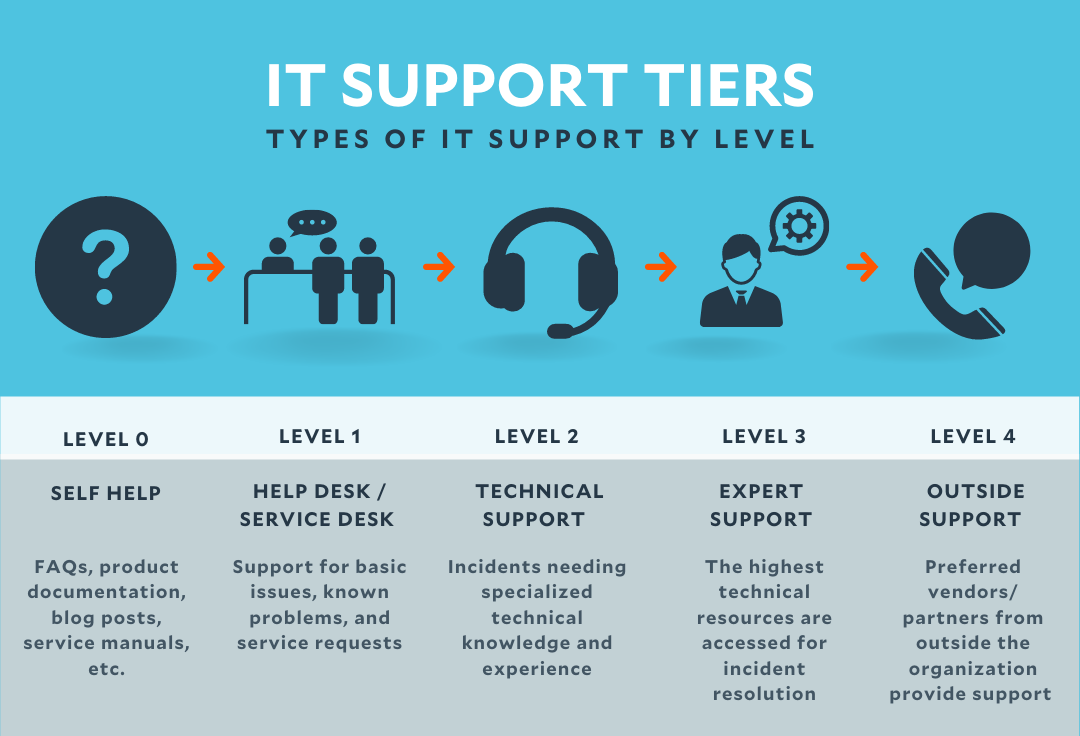
Selecting the Right IT Solutions
When selecting IT solutions, it is essential to think about numerous vital variables to guarantee that the services line up with your business goals. Consider the scalability of the IT solutions to accommodate your business's growth published here and progressing requirements. Furthermore, consider the cybersecurity procedures and protocols executed by the solution carrier to guard your service data and systems.
Applying Cybersecurity Procedures
Executing robust cybersecurity procedures is a crucial facet of guarding your service's delicate data and making sure the stability of your systems. Cyber threats continue to evolve in refinement and learn this here now regularity, making it necessary for services to proactively protect themselves.
Regular safety and security audits and infiltration screening can better assess the performance of your cybersecurity actions and recognize locations for enhancement. By prioritizing cybersecurity and remaining positive in your approach, you can much better shield your business from cyber risks and potential information breaches.
Ensuring Company Connection
After carrying out durable cybersecurity actions to protect your organization's delicate data, the emphasis shifts in the direction of guaranteeing business connection in the face of potential disruptions. Business connection planning is essential for mitigating threats and preserving procedures during unexpected events such as all-natural disasters, cyber-attacks, or system failings. One key element of making sure company connection is the growth of an extensive continuity strategy that details methods for maintaining important features and services. This plan must incorporate procedures for data back-up and recuperation, alternative communication approaches, and worker roles and obligations throughout a crisis.
Additionally, routine testing and updating of the connection plan are vital to ensure its performance when needed. Companies should perform drills and simulations to determine weaknesses in the plan and make essential renovations. In addition, having redundant systems and back-up options in location can assist reduce downtime and ensure smooth operations in situation of disturbances. By focusing on company connection, organizations can enhance their resilience and lessen the effect of potential threats on their operations and reputation.
Verdict

In today's rapidly evolving electronic landscape, the foundation of an effective business exists in the smooth integration of trusted IT support services and durable cybersecurity services.Given the critical function of trustworthy IT support in lessening downtime and boosting cybersecurity, it is important to highlight the considerable benefits that cybersecurity remedies bring to businesses in today's digital landscape.After carrying out durable cybersecurity measures to guard your business's sensitive data, the focus changes towards ensuring company continuity in the try these out face of potential interruptions.In final thought, trusted IT sustain solutions and cybersecurity remedies are essential for equipping organizations to operate efficiently and securely. It is crucial for organizations to prioritize investing in IT support and cybersecurity to secure their procedures and maintain a competitive side in today's digital landscape.